Is your Raspberry Pi a digital fortress or an open door? Securing your Raspberry Pi with SSH is not just a good idea; it's a necessity in today's interconnected world.
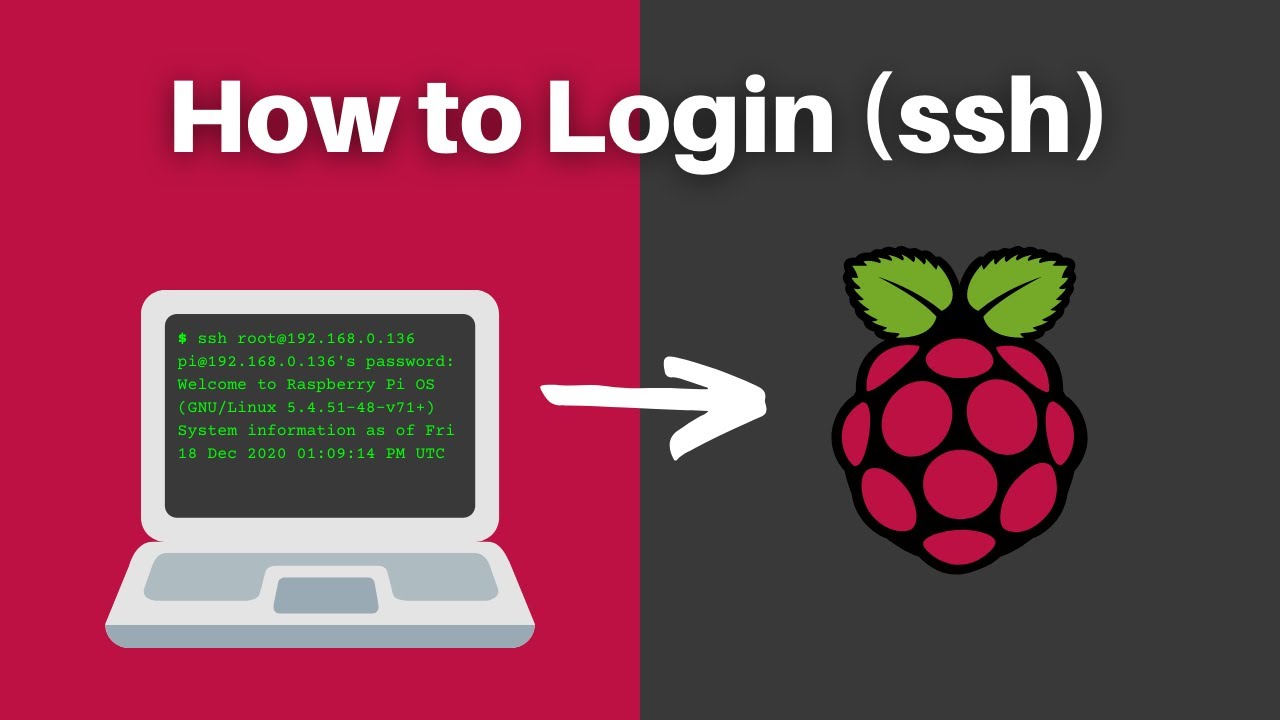
The Raspberry Pi, a versatile and affordable single-board computer, has become a staple for hobbyists, educators, and professionals alike. Its compact size and low power consumption make it ideal for a wide range of applications, from home automation and media servers to robotics and IoT projects. However, the very features that make it so appealing also make it a potential target for security vulnerabilities. One of the most common ways to interact with a Raspberry Pi remotely is through SSH (Secure Shell), and ensuring that this connection is secure is paramount.
| Category | Information |
|---|---|
| General Information | |
| Device Type | Single-Board Computer |
| Typical Use Cases | Home automation, media server, robotics, IoT projects, remote server |
| Operating System | Raspberry Pi OS (formerly Raspbian), Ubuntu, other Linux distributions |
| SSH Configuration | |
| Default SSH Status | Disabled by default for security reasons |
| Enabling Methods | Creating an empty "ssh" file in the /boot partition, using raspberry pi configuration tool |
| Default Port | 22 (can be changed for security) |
| Authentication Methods | Password authentication (less secure), SSH key authentication (more secure) |
| Security Considerations | |
| Vulnerabilities | Default passwords, unencrypted traffic, brute-force attacks |
| Security Measures | Changing default passwords, disabling password authentication, using SSH keys, enabling a firewall (e.g., UFW), using fail2ban |
| File Transfer Protocols | SCP (Secure Copy), SFTP (SSH File Transfer Protocol) |
| Remote Access Alternatives | VNC (Virtual Network Computing) – provides a graphical desktop experience but requires additional security measures |
| Further Resources | Raspberry Pi Official Documentation on Remote Access |